Firewall, Malware Scanner, Two Factor Auth, and Comprehensive Security Features, powered by our 24-hour team. Make security a priority with Wordfence.
WPVulnerability
Hospedagem WordPress com plugin WPVulnerability
Onde devo hospedar o plugin WPVulnerability?
Este plugin pode ser hospedado em qualquer servidor que possua WordPress configurado. Recomendamos fortemente optar por um provedor de hospedagem confiável, com servidores adaptados para WordPress, como o serviço de hospedagem de sites da MCO2.
Hospedando o plugin WPVulnerability em um provedor de confiança
A MCO2, além de instalar o WordPress na versão mais atualizada para seus clientes, oferece o plugin WP SafePress, um mecanismo singular que protege e otimiza seu site ao mesmo tempo.
Por que a Hospedagem WordPress funciona melhor na MCO2?
A Hospedagem WordPress funciona melhor pois a MCO2 possui servidores otimizados para WordPress. A instalação de WordPress é diferente de uma instalação trivial, pois habilita imediatamente recursos como otimização de imagens, proteção da página de login, bloqueio de atividades maliciosas diretamente no firewall, cache avançado e HTTPS ativado por padrão. São recursos que potencializam seu WordPress para a máxima segurança e o máximo desempenho.
This plugin integrates with the WPVulnerability API to provide real-time vulnerability assessments for your WordPress core, plugins, themes, PHP version, Apache HTTPD, nginx, MariaDB, MySQL, ImageMagick, curl, memcached, Redis, and SQLite.
It delivers detailed reports directly within your WordPress dashboard, helping you stay aware of potential security risks. Configure the plugin to send periodic notifications about your site’s security status, ensuring you remain informed without being overwhelmed. Designed for ease of use, it supports proactive security measures without storing or retrieving any personal data from your site.
Data reliability
The information provided by the information database comes from different sources that have been reviewed by third parties. There is no liability of any kind for the information. Act at your own risk.
Using the plugin
WP-CLI
You can use the following WP-CLI commands to manage and check vulnerabilities:
- Core:
wp wpvulnerability core - Plugins:
wp wpvulnerability plugins - Themes:
wp wpvulnerability themes - PHP:
wp wpvulnerability php - Apache HTTPD:
wp wpvulnerability apache - nginx:
wp wpvulnerability nginx - MariaDB:
wp wpvulnerability mariadb - MySQL:
wp wpvulnerability mysql - ImageMagick:
wp wpvulnerability imagemagick - curl:
wp wpvulnerability curl - memcached:
wp wpvulnerability memcached - Redis:
wp wpvulnerability redis - SQLite:
wp wpvulnerability sqlite
To configure the plugin you can use:
- Hide component:
wp wpvulnerability config hide <component> [on|off] - Notification email:
wp wpvulnerability config email <emails>(comma separatted) - Notification period:
wp wpvulnerability config period <never|daily|weekly> - Log retention:
wp wpvulnerability config log-retention <0|1|7|14|28>(in days) - Cache duration:
wp wpvulnerability config cache <1|6|12|24>(in hours)
All commands support the --format option to specify the output format:
--format=table: Displays the results in a table format (default).--format=json: Displays the results in JSON format.
Need help?
wp wpvulnerability --help: Displays help information for WPVulnerability commands.wp wpvulnerability [command] --help: Displays help information for a WPVulnerability command.
REST API
The WPVulnerability plugin provides several REST API endpoints to fetch vulnerability information for different components of your WordPress site.
- Core:
/wpvulnerability/v1/core - Plugins:
/wpvulnerability/v1/plugins - Themes:
/wpvulnerability/v1/themes - PHP:
/wpvulnerability/v1/php - Apache HTTPD:
/wpvulnerability/v1/apache - nginx:
/wpvulnerability/v1/nginx - MariaDB:
/wpvulnerability/v1/mariadb - MySQL:
/wpvulnerability/v1/mysql - ImageMagick:
/wpvulnerability/v1/imagemagick - curl:
/wpvulnerability/v1/curl - memcached:
/wpvulnerability/v1/memcached - Redis:
/wpvulnerability/v1/redis - SQLite:
/wpvulnerability/v1/sqlite
The WPVulnerability REST API uses Application Passwords for authentication. You need to include a valid Application Password in the Authorization header of your requests.
Example Request with Authentication
curl -X GET https://example.com/wp-json/wpvulnerability/v1/plugins -u username:application_password
Replace username with your WordPress username and application_password with your Application Password.
Extra Configurations
“From:” mail (since: 3.2.2)
If, for some reason, you need the emails sent by the plugin to have a From different from the site administrator, you can change it from the wp-config.php by adding a constant:
define( 'WPVULNERABILITY_MAIL', '[email protected]' );
If the constant is active, it will be visible in the configuration screen.
Force hiding checks (since: 4.1.0)
If you want to always hide a specific component, you can define a constant in wp-config.php. When set to true, the option will be checked automatically in the settings screen and the related analysis will be skipped.
Example:
define( 'WPVULNERABILITY_HIDE_APACHE', true );
Available constants: WPVULNERABILITY_HIDE_CORE, WPVULNERABILITY_HIDE_PLUGINS, WPVULNERABILITY_HIDE_THEMES, WPVULNERABILITY_HIDE_PHP, WPVULNERABILITY_HIDE_APACHE, WPVULNERABILITY_HIDE_NGINX, WPVULNERABILITY_HIDE_MARIADB, WPVULNERABILITY_HIDE_MYSQL, WPVULNERABILITY_HIDE_IMAGEMAGICK, WPVULNERABILITY_HIDE_CURL, WPVULNERABILITY_HIDE_MEMCACHED, WPVULNERABILITY_HIDE_REDIS, WPVULNERABILITY_HIDE_SQLITE.
Cache duration (since: 4.1.0)
By default, data from the API is cached for 12 hours.
define( 'WPVULNERABILITY_CACHE_HOURS', 24 );
To change this, define WPVULNERABILITY_CACHE_HOURS in wp-config.php with one of 1, 6, 12 or 24. This value overrides the setting screen and WP-CLI command.
Log rotation (since: 4.2.0)
WPVulnerability stores the most recent API responses so you can review recent calls from the new log tab. Define WPVULNERABILITY_LOG_RETENTION_DAYS in wp-config.php to control how many days of entries are preserved. Supported values are 0, 1, 7, 14 or 28; using 0 disables logging entirely.
define( 'WPVULNERABILITY_LOG_RETENTION_DAYS', 14 );
When the constant is present its value is enforced in the settings UI and through WP-CLI, ensuring consistent log rotation across environments.
Compatibility
- WordPress: 4.7 – 6.9
- PHP: 5.6 – 8.4
- WP-CLI: 2.3.0 – 2.11.0
Security
This plugin adheres to the following security measures and review protocols for each version:
- WordPress Plugin Handbook
- WordPress Plugin Security
- WordPress APIs Security
- WordPress Coding Standards
- Plugin Check (PCP)
- SonarCloud Code Review
Privacy
- This plugin or the WordPress Vulnerability Database API does not collect any information about your site, your identity, the plugins, themes or content the site has.
Vulnerabilities
- No vulnerabilities have been published up to version 4.2.0.
Found a security vulnerability? Please report it to us privately at the WPVulnerability GitHub repository.
Contributors
You can contribute to this plugin at the WPVulnerability GitHub repository.
Capturas de tela

WP-Admin Dashboard widget.
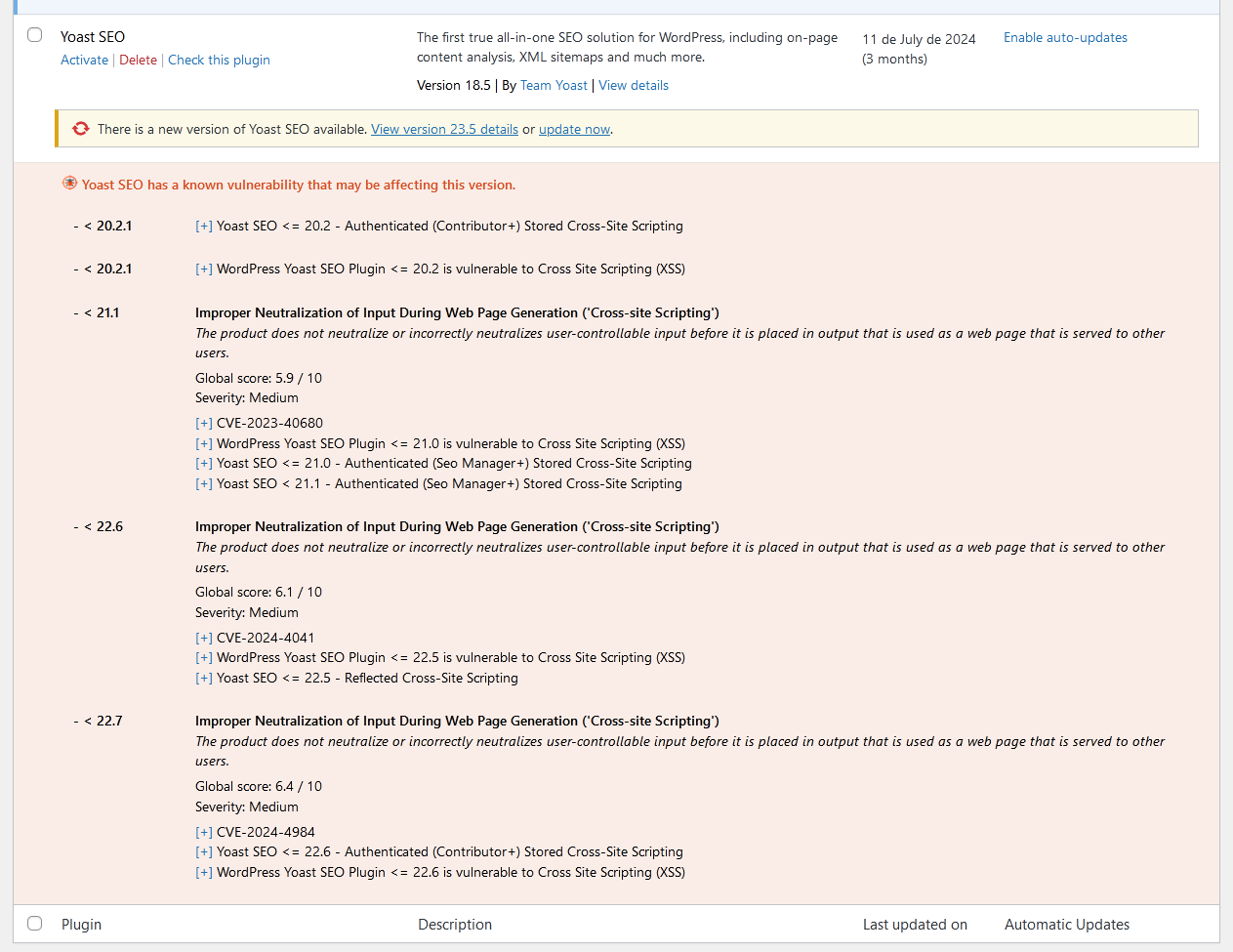
Vulnerability list at Plugins list.

Vulnerability list at Site Health.
